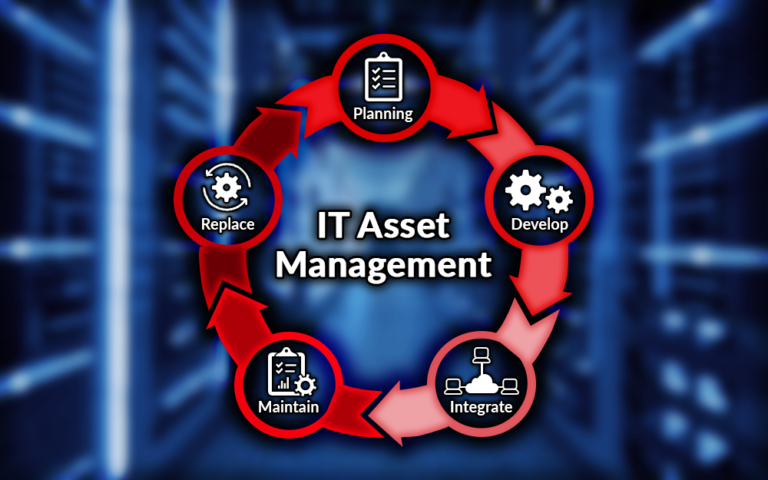
The Simple Security Fix Your Small Business Can’t Afford to Ignore
If your business still relies on passwords alone (single factor authentication) for logins you are putting your organization at risk of a data breach. Hackers (and their automated AI hacking tools) love small businesses because they often lack adequate defenses. But there’s one simple, low-cost (often free!) solution that can block 99.9% of automated attacks: enabling Multi-Factor Authentication…