Thanks for coming back for our deep dive on the Center for Internet Security controls for small business. This week we’ll look at CIS Control #6: Access Control Management – and detail some practical steps you can take to secure and protect your business. Let’s go!
This is one of the most egregiously disregarded controls that I see in small businesses. For instance, do you have a single shared account that you use to access some aspect of your business data? Everyone knows the password and, if anything went wrong, you wouldn’t have a clear idea of who was logged in at the time?
I worked with an auto repair shop recently that had experienced an employee embezzling money from the company, and since there were not separate accounts for employees to access that data (that they shouldn’t have had access to in the first place) it took much longer than it should have to catch the thief.
Does any of this sound familiar? Read on.
The full verbiage from CIS: Use processes and tools to create, assign, manage, and revoke access credentials and privileges for user, administrator, and service accounts for enterprise assets and software.
Why should we worry about this?
Weak access controls are a major attack surface for organizations:
- Insider threats account for 34% of data breaches, often due to excessive or unnecessary access rights
- 80% of hacking-related breaches involve compromised or weak credentials
- 62% of businesses experienced phishing and social engineering attacks aimed at stealing login credentials
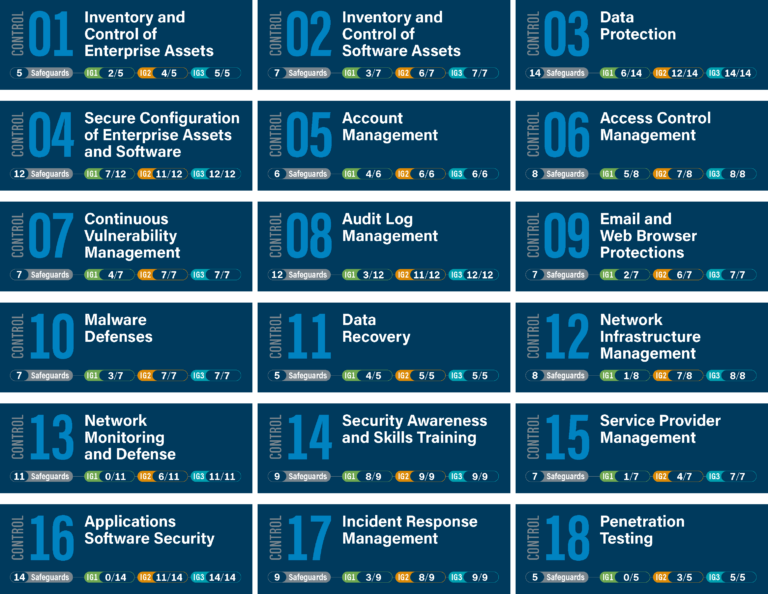
What is CIS Control 6?
CIS Control 6 focuses on managing access rights to systems and data. It’s about ensuring that only the right people have access to the right information at the right time. Think of it as the bouncer for your digital nightclub – it decides who gets in and what areas they can access.
Why is it Crucial for Small Financial Businesses?
- Protects Sensitive Data: In finance, data is your most valuable asset. Proper access control ensures that sensitive financial information doesn’t fall into the wrong hands.
- Prevents Insider Threats: Not all threats come from outside. CIS Control 6 helps manage access within your organization, reducing the risk of internal data breaches.
- Ensures Regulatory Compliance: Financial institutions face strict regulations. Proper access control is often a key requirement for compliance with standards like ISO 27001, SOC II, and industry-specific regulations.
- Maintains Client Trust: Your clients trust you with their financial data. A breach due to poor access control can irreparably damage that trust.
Implementing CIS Control 6 in Your Small Business
Here are practical steps to implement CIS Control 6:
- Conduct an Access Audit: Start by mapping out who has access to what in your systems.
- Implement the Principle of Least Privilege: Give employees access only to the data and systems they need for their specific roles.
- Use Multi-Factor Authentication (MFA): Implement MFA for all user accounts, especially those with access to sensitive data.
- Regularly Review and Update Access Rights: People’s roles change. Make sure their access rights change with them.
- Implement Strong Password Policies: Require complex passwords and regular changes.
- Monitor and Log Access: Keep track of who’s accessing what and when. This can help detect unusual activities.
- Automate Access Management: Consider using Identity and Access Management (IAM) tools such as Microsoft Azure Active Directory or Entra ID.
Remember, in cybersecurity, you’re only as strong as your weakest link. Don’t let poor access control be that weak link. Start implementing CIS Control 6 today – your organizations future may depend on it.
Have questions about implementing CIS Control 6 in your business? Drop a comment below or get in touch with any questions you might have.
You can read more about the CIS Security Controls framework at the Center for Internet Security website, and find all 18 controls listed here.
Stay secure, stay successful!
Michael @ MZ DATA
Long Beach, CA